Friday, July 30, 2010
The cost of a Hendrix covermount
Blackburne J was clear the defendant did have reasonable grounds to know that it was infringing as Experience Hendrix had challenged them prior to publication, though the paper was not recklessly indifferent to the problem – so damages would not be increased by reference to flagrancy or ‘moral prejudice’. Article 13 of the Enforcement Directive (2004/48/EC) sets out different damages regimes depending on the defendant’s knowledge, though it seems unclear that this altered the judge’s calculations.
At the time of the covermount the claimants were themselves intending to release a film of the concert plus accompanying DVD, CD and merchandising. Following the covermount this project was put on hold because (1) the claimants wanted a declaratory judgment that they owned the rights because (a) the rights dispute could scare off their project’s commercial sponsors and (b) the Sunday Times’s ultimate licensor, Charly, could go and do more damage elsewhere and (2) the covermount had spoiled the market for the claimants’ products. The judge was not convinced by the defendant’s arguments that (i) the problem with Charly existed irrespective of the covermount and (ii) the defendants could not be blamed for the effects of the claimants’ decision to suspend their project if that had been misjudged.
The judge held that:
1. If there had been no covermount the claimant’s project could have been launched in July 2007 though given the lack of urgency about the project September was more likely.
2. The delay caused to the claimants by the covermount distribution was one year. The claimants obtained declaratory relief in February 2008 and the spoiling of the market by the covermount was also no obstacle by February 2008 (if indeed the market had been spoiled at all).
3. The claimants could expect to be compensated in relation to the effect on their normal exploitation of the rights (was the claimant in the business of selling copies or licensing rights?). Here the claimants were planning to release a film etc, so those losses should be assessed.
4. The damages could cover economic loss outside the UK in as much as it stemmed from the infringement of UK copyright.
5. Quantum: difficult as the claimants have not yet gone ahead with their project. It was uncertain whether they would make any less money because their project had been delayed.
6. The covermount deprived the defendants of $5.8 million for 12 months.
7. The loss the defendants incurred by having the receipt of this sum delayed would be US base rate + 1% on $5.8 million over one year. That was considerably less than the sum the claimants were looking for.
It's official...
 This copyright law enthusiast is officially pleased to be one of the new members of the fabulous 1709 Blog team. In future, I shall endeavour to bring news of the latest developments in German copyright law to an English-speaking audience. Why? Because I believe Lord Goff of Chieveley was clearly on to something when he suggested we “sufficiently dispel our ignorance of German law and so by comparison illuminate our understanding of our own.” (White v Jones [1995] 2 AC 207)
This copyright law enthusiast is officially pleased to be one of the new members of the fabulous 1709 Blog team. In future, I shall endeavour to bring news of the latest developments in German copyright law to an English-speaking audience. Why? Because I believe Lord Goff of Chieveley was clearly on to something when he suggested we “sufficiently dispel our ignorance of German law and so by comparison illuminate our understanding of our own.” (White v Jones [1995] 2 AC 207)In an interesting recent case, the Regional Court of Cologne (LG Köln) had to decide what constitutes a so-called official work (LG Köln, Urteil vom 07.07.2010 – 28 O 721/09).
That certainly seems clear enough, but the case at hand shows that there may be difficulties involved: Claimant was an attorney; defendant operated a website with reports on legal disputes. Claimant, acting for one of his clients, sought a preliminary injunction (PI) against defendant from a court in Berlin. The court granted the PI, stating:
“The preliminary injunction had to be granted for the reasons set out in the attached motion for the preliminary injunction including the appendices thereto.”
Subsequently, defendant published claimant’s brief on his website, as part of an article about his objection proceedings against the PI. Claimant sued for copyright infringement, so the LG Köln had to decide whether in this context the attorney’s brief was part of an official work for the purposes of section 5(1) UrhG.

I believe the court struck a fair balance of interests, given that the publication of the PI would be quite pointless if it were not permitted to publish the motion for the PI as well. Also, I like my PIs super fast and do not think judges should be made to paraphrase the arguments submitted in an attorney’s brief if they happen to agree with them. Do readers feel the same way, or do you think that’s just promoting laziness?
Thursday, July 29, 2010
Your Ally In The Android vs iPhone Battle
 Is texting or email an important part of your mobile activities? If so, you’ll love the ability to use real keys instead of poking at a glass screen. The LG Ally offers both a 3.2 inch touch screen and a slide out full QWERTY keyboard with nicely sized physical keys. You’ve got 5 home screens to customize, so just go nuts with those Android apps.
Is texting or email an important part of your mobile activities? If so, you’ll love the ability to use real keys instead of poking at a glass screen. The LG Ally offers both a 3.2 inch touch screen and a slide out full QWERTY keyboard with nicely sized physical keys. You’ve got 5 home screens to customize, so just go nuts with those Android apps.This is also a social networking phone. The included LG Socialite widget lets you manage your Facebook and Twitter accounts simultaneously. Why have to choose when you can have both? What fun is voicemail unless you can view and manage it on your cell phone. This one has that capability.
As you can see, the LG Ally has some unique capabilities. But it also has all the standard Internet and multimedia capabilities that you expect in an advanced smartphone. Text message and multimedia messaging are built-in. So is an email client that supports push Gmail and Exchange. The Android Webkit HTML5-based Web browser puts the Web at your fingertips. Verizon’s 3G EVDO Rev A network and WiFi access connect you to the bandwidth you need to access the Web with ease.
You’re all set up to capture what you see with the 3.2 Megapixel digital camera. This one has modes similar to many higher priced digital cameras. You get night mode, macro mode, panorama, smile detection and beauty shot. Flash and auto-focus are part of this camera, as well as the ability to use it as a camcorder to capture videos that you can share with friends or your social network right from the phone.
Other useful features include integrated GPS that provides spoken turn-by-turn directions and real time traffic updates, MP3 player that lets you download MP3s from the Amazon Music Store, streaming multimedia support, Stereo Bluetooth so that you can stream your music in high quality to headphones and other compatible devices, and a lot more.
Does the this sound like the type of smartphone you’ve been looking for if you could afford it? Well, you can. Right now the LG Ally is free when you order it with new Verizon Wireless service. That deal may not last for long, so go for it this is the phone for you.
If you prefer, you can check out all the Android phones and other cell phone special offers now available through Cell Phone Plans Finder.

Do you dare to play this game – can you hack it?
 You are ‘C’, a.k.a. head of MI6. You are playing a game of evasion, a game where you have no equals. That is, not until now. It’s time, time for you to come face to face with your nemesis . . . ‘Z’.
You are ‘C’, a.k.a. head of MI6. You are playing a game of evasion, a game where you have no equals. That is, not until now. It’s time, time for you to come face to face with your nemesis . . . ‘Z’.Go deep into the Copyright, Designs and Patents Act 1988 and there you will find ‘Z’ – a.k.a. ‘the Z sections’.
Yesterday Mr Justice Floyd considered section 296ZD in the summary judgment of Nintendo v Playables. It’s a case that examines the UK’s law regarding circumvention of copyright protection – and whether there’s a difference in the law when it is computer programs that are being copied, or other copyright works.
It all began with a customs seizure of 165,000 devices – devices that are used by those who enjoy playing a game of cat and mouse with Nintendo. Here’s how to play:
1. Illegally download games from the internet (instead of paying £20–£30 per game).
2. Copy games on to illegal device.
3. Slot device into Nintendo DS.
4. DS checks games are genuine – device gives DS the all clear.
5. Play!
Once the judge had resolved concerns about the fact that this uncontested summary judgment application came before him after the parties had partially settled, he easily granted summary judgment finding infringement under ss. 296 and 296ZD.
Sections 296 and 296ZD
These sections outlaw making or selling means for circumventing technological measures that protect copyright. Section 296 applies where the copyright being infringed is in computer programs. Section 296ZD applies where other types of copyright are being targeted.
Floyd J held that s. 296ZD was applicable in this case (as well as s. 296) because ‘although that which is stored on the card is a computer program, the game includes graphic and other works the copying and use of which is controlled by the ETM.’ (Don’t most computer programs involve some copyright material apart from code?)
On the face of it s. 296 requires that the defendant knows the circumventing technology will, at some point, be used to infringe copyright. However, this reading should be questioned as the section implements the Computer Programs Directive, which does not require the defendant to have this knowledge. Under s. 296ZD, by contrast, it’s clearly immaterial whether the defendant (‘C’) knew the device would be used for infringing copyright.
 Playables’ export sales
Playables’ export salesIn Sony v Ball, Laddie J held that ss. 296 and 296ZD would not apply where the devices were used abroad. Floyd J went along with this for s. 296 as it applies where the defendant knows devices would be used to make ‘infringing copies’ (i.e. copies that infringe UK copyright). However, the ‘infringing’ language is missing from s. 296ZD, so Floyd J, reluctantly departing from Laddie, held that s. 296ZD would apply to exported devices.
Under this line of reasoning, it would seem that had Parliament correctly implemented EU law, s. 296 might also apply to exported devices….
The judge’s view gives UK law in relation to copyright-protection devices a kind of extra-territorial effect that is not present in normal authorization of copyright infringement (where the copyright infringement that has been authorized must take place in the UK).
Now for a game of s. 16…
Presumably because these devices can be used for playing home-made games, the judgment makes no mention of Playables authorizing copying of Nintendo’s games but there was still some scope for an old-fashioned game of s. 16 copyright.
Playables, it was held, was authorizing the copying of the ‘NLDF’ security code from the device to the DS’s RAM. It isn’t mentioned, but aren’t the devices also sold holding an illicit copy of the NLDF?
When a user puts the device into the console, the DS’s boot-up software is copied into the DS’s RAM. Floyd J was not quite ready to grant summary judgment – it seems because legal Nintendo cards would have the same effect. Surely, however, even though the two copies are identical, one is authorized and the other isn’t?
As for the Nintendo Racetrack Logo, the judge said it was ‘so rudimentary that I consider that it is arguable that copyright does not subsist, particularly as what it is relied on is a modification of a pre-existing work’. Once you’ve experienced the state-of-the-art game of ‘Z’, a game of s. 16 can start to seem a bit basic and old-hat.
Jailbreaking through a pile of bricks
 As blogger Jeremy reported here, the U.S. Library of Congress issued a statement on Monday that legalized “jailbreaking” wireless telephone handsets. Jailbreaking is a process of modifying the device’s security software in order to enable interoperability with legally obtained software applications or to connect to an alternative network if the alternative network operator authorizes the connection.
As blogger Jeremy reported here, the U.S. Library of Congress issued a statement on Monday that legalized “jailbreaking” wireless telephone handsets. Jailbreaking is a process of modifying the device’s security software in order to enable interoperability with legally obtained software applications or to connect to an alternative network if the alternative network operator authorizes the connection. This exemption to the Digital Millennium Copyright Act (DMCA) applies equally to all wireless telephone handsets, their manufacturers and their network operators. However, if the consumer and media frenzy in the past few days are any reflection, it would seem to have been written specifically to address Apple’s iron hold over U.S. users of the iPhone, who are typically required to purchase apps from the Apple App Store and to use only AT&T wireless network service. (Apple lobbied aggressively against this DMCA exemption.) To counter previous instances of jailbreaking, Apple had used its operating system upgrades, which automatically install on active iPhones, to lock any unauthorized software. Locking the unauthorized software essentially rendered the phones as useless as a brick for communication purposes (leading to this tactic being known as “bricking the iPhone”). In addition, Apple warned users that jailbreaking violated and invalidated their warranty, so users could not seek free assistance or services from Apple technicians if the user experienced trouble with their iPhone. Apple claimed these consequences were justified because the jailbreaker had violated copyright law.
 Then again, looking at this comparison chart, maybe the iPhone isn't that different from a brick after all....
Then again, looking at this comparison chart, maybe the iPhone isn't that different from a brick after all.... With jailbreaking now legal under copyright law, will Apple continue bricking phones and refusing to service legally jailbroken phones? Apple has already issued a statement reiterating that jailbreaking invalidates its warranty. And it retains the right to do so under the terms of its warranty and user agreements. But will Apple be able to continue the practice of bricking phones during operating system upgrades? Doing so, it seems to me, punishes users for an action that is now perfectly legal under copyright law. It is one thing to invalidate a warranty and refuse free system services, but quite another to render the product inoperable. If anyone has thoughts on Apple’s bricking policy, please feel free to leave comments below.
And if you’re a U.S. iPhone owner considering a jailbreak, I’ve heard that T-Mobile USA offers technical support (to replace the invalidated Apple warranty) to iPhone owners who subscribe their jailbroken iPhones with T-Mobile service.
Obsolete dongles to become history?
 Thanks are due to my friend and fellow blogger Miri Frankel (IP Finance) for drawing my attention to a recent statement by the Librarian Congress relating to classes of works to be exempted from the statutory prohibition under the Digital Millennium Copyright Act (DMCA) against circumventing technological means that prevent access to it. Miri suggests that the two exemptions that will have the biggest impact are likely be (i) the unlocking of phones in order to use otherwise inoperable apps and to use them on other carriers' networks and (ii) circumventing DVD security in order to use materials for educational purposes, comment or criticism. The statement reads thus, in relevant part:
Thanks are due to my friend and fellow blogger Miri Frankel (IP Finance) for drawing my attention to a recent statement by the Librarian Congress relating to classes of works to be exempted from the statutory prohibition under the Digital Millennium Copyright Act (DMCA) against circumventing technological means that prevent access to it. Miri suggests that the two exemptions that will have the biggest impact are likely be (i) the unlocking of phones in order to use otherwise inoperable apps and to use them on other carriers' networks and (ii) circumventing DVD security in order to use materials for educational purposes, comment or criticism. The statement reads thus, in relevant part:"Statement of the Librarian of Congress Relating to Section 1201 Rulemaking
Section 1201(a)(1) of the copyright law requires that every three years I am to determine whether there are any classes of works that will be subject to exemptions from the statute’s prohibition against circumvention of technology that effectively controls access to a copyrighted work. I make that determination at the conclusion of a rulemaking proceeding conducted by the Register of Copyrights, who makes a recommendation to me. Based on that proceeding and the Register’s recommendation, I am to determine whether the prohibition on circumvention of technological measures that control access to copyrighted works is causing or is likely to cause adverse effects on the ability of users of any particular classes of copyrighted works to make noninfringing uses of those works. The classes of works that I designated in the previous proceeding expire at the end of the current proceeding unless proponents of a class prove their case once again.
This is the fourth time that I have made such a determination. Today I have designated six classes of works. Persons who circumvent access controls in order to engage in noninfringing uses of works in these six classes will not be subject to the statutory prohibition against circumvention.
... it is important to understand the purposes of this rulemaking, as stated in the law, and the role I have in it. This is not a broad evaluation of the successes or failures of the DMCA. The purpose ... is to determine whether current technologies that control access to copyrighted works are diminishing the ability of individuals to use works in lawful, noninfringing ways. The DMCA does not forbid the act of circumventing copy controls, and therefore this rulemaking proceeding is not about technologies that control copying. Nor is this rulemaking about the ability to make or distribute products or services used for purposes of circumventing access controls, which are governed by a different part of section 1201. ...
The six classes of works are:
(1) Motion pictures on DVDs that are lawfully made and acquired and that are protected by the Content Scrambling System when circumvention is accomplished solely in order to accomplish the incorporation of short portions of motion pictures into new works for the purpose of criticism or comment, and where the person engaging in circumvention believes and has reasonable grounds for believing that circumvention is necessary to fulfill the purpose of the use in the following instances: (i) Educational uses by college and university professors and by college and university film and media studies students; (ii) Documentary filmmaking; (iii) Noncommercial videos
(2) Computer programs that enable wireless telephone handsets to execute software applications, where circumvention is accomplished for the sole purpose of enabling interoperability of such applications, when they have been lawfully obtained, with computer programs on the telephone handset.
(3) Computer programs, in the form of firmware or software, that enable used wireless telephone handsets to connect to a wireless telecommunications network, when circumvention is initiated by the owner of the copy of the computer program solely in order to connect to a wireless telecommunications network and access to the network is authorized by the operator of the network.
(4) Video games accessible on personal computers and protected by technological protection measures that control access to lawfully obtained works, when circumvention is accomplished solely for the purpose of good faith testing for, investigating, or correcting security flaws or vulnerabilities, if (i) The information derived from the security testing is used primarily to promote the security of the owner or operator of a computer, computer system, or computer network; and (ii) The information derived from the security testing is used or maintained in a manner that does not facilitate copyright infringement or a violation of applicable law.
(5) Computer programs protected by dongles that prevent access due to malfunction or damage and which are obsolete. A dongle shall be considered obsolete if it is no longer manufactured or if a replacement or repair is no longer reasonably available in the commercial marketplace; and
(6) Literary works distributed in ebook format when all existing ebook editions of the work (including digital text editions made available by authorized entities) contain access controls that prevent the enabling either of the book’s read-aloud function or of screen readers that render the text into a specialized format ..."My initial scepticism that the US approach to technological circumvention and copyright has somewhat evaporated of late, when I contrast the flexible functionality of the position in the US with the principled paralysis of Europe. Am I alone?
Communication questions: Romania asks the oracle
 The Inalta Curte de Casatie si Justitie (Romania) has referred some copyright questions to the Court of Justice of the European Union for preliminary rulings in Case C-283/10 Circ & Variete Globus Bucureşti v Uniunea Compozitorilor şi Muzicologilor din România - Asociaţia pentru Drepturi de Autor - U.C.M.R. - A.D.A. -- yet another case that can't be located on the Curia website. This case regards communication of musical works to the public and collective management under Directive 2001/29 of the European Parliament and of the Council of 22 May 2001 on the harmonisation of certain aspects of copyright and related rights in the information society. The referring court asks:
The Inalta Curte de Casatie si Justitie (Romania) has referred some copyright questions to the Court of Justice of the European Union for preliminary rulings in Case C-283/10 Circ & Variete Globus Bucureşti v Uniunea Compozitorilor şi Muzicologilor din România - Asociaţia pentru Drepturi de Autor - U.C.M.R. - A.D.A. -- yet another case that can't be located on the Curia website. This case regards communication of musical works to the public and collective management under Directive 2001/29 of the European Parliament and of the Council of 22 May 2001 on the harmonisation of certain aspects of copyright and related rights in the information society. The referring court asks: "1. Is Article 3(1) of Directive 2001/29 ... to be interpreted to the effect that 'communication to the public' means:
(a) exclusively communication to the public where the public is not present at the place where the communication originates, or
(b) also any other communication of a work which is carried out directly in a place open to the public using any means of public performance or direct presentation of the work?
In the event that point (a) represents the correct meaning, does that mean that the acts, referred to in point (b), by which works are communicated directly to the public do not fall within the scope of that directive or that they do not constitute communication of a work to the public, but rather the public performance of a work, within the meaning of Article 11(1)(i) of the Berne Convention?
2. In the event that point (b) represents the correct meaning, does Article 3(1) of the directive permit Member States to make statutory provision for the compulsory collective management of the right to communicate musical works to the public, irrespective of the means of communication used, even though that right can be and is managed individually by authors, no provision being made for authors to be able to exclude their works from collective management?"
 The 1709 Blog received this information from the UK's Intellectual Property Office, which somewhat alarmingly gives us only till tomorrow, 30 July, to email our comments to the Office. Like NIPC's colleague Jane Lambert (who has posted a helpful note here), he's not sure exactly what the background to this is, though it seems that the parties are, respectively, a circus and a rights society. All further information is gratefully received.
The 1709 Blog received this information from the UK's Intellectual Property Office, which somewhat alarmingly gives us only till tomorrow, 30 July, to email our comments to the Office. Like NIPC's colleague Jane Lambert (who has posted a helpful note here), he's not sure exactly what the background to this is, though it seems that the parties are, respectively, a circus and a rights society. All further information is gratefully received.
Wednesday, July 28, 2010
Cash In With Custom Toll Free Numbers
 What’s so important about a toll free number? It’s not that the numbers themselves are magic. It’s the tremendous investment, both in advertising cost and sweat equity, that go into making that number synonymous with the business. You see them advertised on television, on the radio, in print and online. The catchier the toll free number and the more you associate it with a particular business, the more value it has. Do any of these examples happen to ring a bell (so to speak)?
What’s so important about a toll free number? It’s not that the numbers themselves are magic. It’s the tremendous investment, both in advertising cost and sweat equity, that go into making that number synonymous with the business. You see them advertised on television, on the radio, in print and online. The catchier the toll free number and the more you associate it with a particular business, the more value it has. Do any of these examples happen to ring a bell (so to speak)? 1-800-flowers
1-800-contacts
1-800-petmeds
Note: These aren't just numbers that come to mind, they are also among the top ones listed by Google for "1-800". This shows that toll free numbers even help you get noticed on the Internet.
How about your business? Do people have an easy way to get in contact with you? Will they remember when it comes time to acquire your goods or services? Or will they just get out the yellow pages and call some ad they happen on or walk into the nearest store that looks like it might have what they need?
If you’ve got a substantial business or aspire to be one, getting an easy to remember toll free number can be just the hook you need. It’s even better if the number spells out the name of your business or what you do. These are called vanity numbers for obvious reasons. But the term vanity is much too shallow to describe the value of these assets. They should probably be called golden numbers or licenses to print money.
Now, the big question. How do you find these numbers? They must all be taken already, right?
Wrong, wrong, wrong. Of course, some of the best are taken. Toll free numbers didn’t just pop up yesterday (I’ll tell you about an exception in just a second). But there are many, many combinations that are available and ready for you to order right now. Don’t get a headache straining your brain to come with clever slogans or strain your eyes starting at the telephone keypad. Make the search easy with a FREE toll free number search.
Just enter the name of your business, product, service or something like that. That’s good enough to get started. This search tool will automatically convert your text to numbers and then search a database of millions of toll free numbers to the closest matches. You’ll see a list of possibilities displayed. Pick one of those or try some other phrases to see what pops up.
Now here’s something not too many people know. There’s a new toll free number becoming available soon. You already know about 800, 866, 877 and 888 prefixes. They’re all toll free. On October 1, 2010 at exactly 12:00 PM EST the prefix 855 will be released by the FCC. It’s going to be like a land rush, and perhaps more valuable. If you’ve got something in mind but your number combinations are all taken, then you want to reserve your 855 toll free number now.
Want to have some fun and perhaps buy yourself a valuable asset in the process? Go ahead and try some toll free number searches now. It doesn’t cost anything to look and you never know what you’ll find.

The trade mark's a killer for Eugenia Padilla
 Copyright is not a subject that often crops up in Community trade mark disputes, but it did here in Case T‑255/08, Eugenia Montero Padilla v Office for Harmonisation in the Internal Market, José María Padilla Requena -- an appeal to the General Court against the refusal of the office that administers the Community trade mark system to block the registration of the JOSE PADILLA trade mark. Essentially what we have here is one good soul named José Padilla trying to register the name JOSE PADILLA as a trade mark, with another lady -- who appears to administer the copyright of her uncle (a composer of that name) -- seeking to stop her.
Copyright is not a subject that often crops up in Community trade mark disputes, but it did here in Case T‑255/08, Eugenia Montero Padilla v Office for Harmonisation in the Internal Market, José María Padilla Requena -- an appeal to the General Court against the refusal of the office that administers the Community trade mark system to block the registration of the JOSE PADILLA trade mark. Essentially what we have here is one good soul named José Padilla trying to register the name JOSE PADILLA as a trade mark, with another lady -- who appears to administer the copyright of her uncle (a composer of that name) -- seeking to stop her.Eugenia argued first that, if her adversary were allowed to register the mark, she wouldn't be able to gain the benefit of the presumption that a person named as the author of a published work is its author, under Article 5 of the IP Enforcement Directive. She later argued that, since the name "José Padilla" was attached to copies of the composer's copyright-protected works (CDs, DVDs, sheet music etc) sold in the course of trade, that constituted the use of a trade mark which would be able to thwart a later attempt by someone else to register the mark.
Serious damages
It is not just the titles of the author’s books that is worthy of note, however, but also the method of calculating damages:
Number of copies sold by Astrel x £2400 approx (price of claimant’s luxury six-volume leather-bound edition)
Astrel’s edition sold for around £3.40.
The judgment may be intended to demonstrate Russia’s willingness to take IP enforcement seriously – an issue blocking its entry to the World Trade Organization. But how reassuring will the WTO find this financial methodology?
Tuesday, July 27, 2010
Business Ethernet Vs T1
 Business Ethernet, also known as Metro Ethernet, Ethernet over Copper and Ethernet over Fiber, offers scalable higher bandwidths, lower cost per Mbps, and increasing availability. It’s called “Business Ethernet” to emphasize that Ethernet isn’t just for LANs and carriers anymore. It’s being rapidly deployed into the SMB arena.
Business Ethernet, also known as Metro Ethernet, Ethernet over Copper and Ethernet over Fiber, offers scalable higher bandwidths, lower cost per Mbps, and increasing availability. It’s called “Business Ethernet” to emphasize that Ethernet isn’t just for LANs and carriers anymore. It’s being rapidly deployed into the SMB arena.What’s so great about Ethernet? It’s now the universal standard for computer networking. Nearly every desktop PC, router, switch, and cabling infrastructure is designed to support Ethernet. Manufacturing economies of scale ensure that it will be tough, indeed, for another other technology to bee the price/performance of Ethernet.
The proliferation of Ethernet has also caused telecom carriers to rethink their public networks. T1 lines, DS3 bandwidth and OCx services are all based on circuit switched standards established to transport telephone calls. Ethernet is a packet switched technology that can be carried on circuit switched networks. With most networks now packet switched, it only makes sense to make the telecom networks packet switched also.
Packet switching end-to-end offers some interesting possibilities. If the LAN, MAN and WAN all support Ethernet, then you can establish level 2 switching to interconnect multiple business locations. Each location has its own LAN and they are tied together with MAN and WAN Ethernet services. You are extending your company network to encompass the connections between locations as well.
Business Ethernet is a scalable service. That means you can order a range of bandwidths for your connection, also called a port. As long as you stay within the capacity of the port, you can often get bandwidths in small increments including 1 Mbps. That way, you can order just the amount of bandwidth you need today, but can quickly upgrade with a phone call to your provider when business increases and you need more. It’s a great strategy to optimize costs and still get the performance you need right now.
How about the cost comparison with T1? It varies somewhat with location and the amount of competition for your business, but it’s not unusual to get 3 Mbps Ethernet for what you pay now to get a 1.5 Mbps T1 line. A popular service is 10 Mbps Ethernet. That costs about what you were paying for T1 a contract or two ago.
One service of particular note is Ethernet over Copper. This technology uses special terminal equipment installed by the service provider to bond multiple copper pair for your telecom connection. This gives bandwidths up to 50 Mbps over already installed copper wiring so you don’t have to pay for a new fiber installation. T1 lines can also be bonded, but the bandwidth tops out at 10 or 12 Mbps.
Which service is right for your business? They’re both professional grade and highly reliable digital line services. Why not get a set of competitive quotes for T1 vs Business Ethernet and see which will save you the most money?


Monday, July 26, 2010
Finding An Ethernet Internet Provider

The Ethernet Internet Finder is your one-stop service for locating Ethernet Internet providers and getting competitive service quotes. It’s affiliated with Telarus, Inc., the renowned telecom services broker, and connects to their patented GeoQuote software and suite of expert consultants. All you do is enter some basic company contact information and you are good to go. Try to enter the main telephone number at the business rather than a cell phone, as the system uses this information to help find service availability and pricing.
Don’t worry about getting charged for any of this. The Ethernet Internet Finder is free to use for any serious business purpose. The friendly consultants will go over the range of services available for your location and make recommendations for how you can get the most bandwidth for the least cost. Yes, you need a location that is listed for business use for this to work. If you are working from a home office or want residential service, we recommend “Can I Get DSL?” to find your best options for DSL, Cable, 4G wireless, fiber to the home, and satellite broadband.
In case you are not familiar with Ethernet Internet access, this is a fairly new bandwidth service that is growing by leaps and bounds. It provides an Ethernet connection from your local area network, which is already running Ethernet, to the Internet, which is highly compatible with Ethernet. Traditional telecom connections were designed to transport telephone calls and are not as efficient as what’s known as Metro or Carrier Ethernet. There are also many new providers who specialize in Ethernet and IP networks that are anxious to compete for your business.
As a result, you can generally save money when you switch to Ethernet Internet service. How much? It’s not unusual to get twice the bandwidth for the same cost using Ethernet at 3 Mbps vs a T1 line at 1.5 Mbps. The higher the bandwidth, the lower the price per Mbps.
Also, new Ethernet over Copper (EoC) technology can deliver 10 Mbps Ethernet connections to your business using existing twisted pair copper wiring. You don’t necessarily have to bring in new fiber optic service to get the bandwidth you need. How much bandwidth can you get and for what cost? The easy way to find out is to use the Ethernet Internet Finder now.


Sunday, July 25, 2010
MPLS Bandwidth A Bargain
You’ve heard of cloud networks? MPLS is a cloud networking technology. This is different that cloud computing or cloud storage because MPLS is only about making connections. Whether you do anything within the cloud is another matter. This is about transport, or getting packets from point to point.
MPLS networks are privately owned and operated. If you want to get on the MPLS network, you’ll need to make arrangements with a MPLS service provider. It’s not like the Internet, which is open to anyone and everyone. The advantage of this premium-grade bandwidth service is that the MPLS network operator can guarantee bandwidth and quality of service.
But doesn’t premium-grade mean premium price? Not really. You need to compare apples to apples. In this case, you need to compare what you pay to use the MPLS network with what it costs to maintain the same quality connections another way. Traditionally, that other way has been proprietary company networks constructed from dedicated point to point lines or Frame Relay Networks.
Frame Relay is actually the ancestor to MPLS. It was developed for the same purpose. That was to connect geographically diverse locations with reliable and secure data links. Frame Relay networks served us well for decades. But they were designed in an era of much lower bandwidths, prior to the onslaught of audio, video and massive file sizes.
MPLS is the upgrade to Frame Relay. It can handle anything you need to transport in any format. The letters M-P-L-S stands for Multi-Protocol Label Switching. Multi-Protocol means that this network can handle voice, data, video and even TDM services such as switched circuit telephony. The built-in quality of service mechanisms ensure that each service gets the network characteristics it needs. You don’t have to worry about large data transfers causing your phone calls to drop.
The bargain pricing offered by MPLS networks is that the cloud is efficiently utilized to handle traffic from multiple clients. That way, you are only paying for what you need. You can always add more locations or bandwidth if the need arises. Try doing that with proprietary networks.
Does MPLS offer a cost savings for your operations? Find out with a MPLS network competitive price quote. It’s fast, easy and free.


Saturday, July 24, 2010
Software analytics: idea and expression
 On Friday Mr Justice Arnold delivered a judgment in the dispute between SAS Institute Inc (a major player in the business analytics software market) and World Programming Ltd. As the judgment sets out:
On Friday Mr Justice Arnold delivered a judgment in the dispute between SAS Institute Inc (a major player in the business analytics software market) and World Programming Ltd. As the judgment sets out:‘The Defendant, World Programming Ltd ("WPL"), perceived that there would be a market demand for alternative software which would be able to execute application programs written in the SAS Language. WPL therefore created a product called World Programming System or WPS to do this. In developing WPS, WPL sought to emulate much of the functionality of the SAS Components as closely as possible in the sense that, subject to only a few minor exceptions, it tried to ensure that the same inputs would produce the same outputs. This was so as to ensure that WPL's customers' application programs executed in the same manner when run on WPS as on the SAS Components. There is no suggestion that in doing so WPL had access to the source code of the SAS Components or that WPL have copied any of the text of the source code of the SAS Components or that WPL have copied any of the structural design of the source code of the SAS Components.’In the judge’s view replicating the functionality of the SAS software did not infringe copyright, but WPL’s manuals did – though you would expect the manuals to bear some resemblance to the SAS manuals there was a degree of similarity in the language that went beyond the inevitable.
 This is not the end of the story, however. The judge’s views are conditional. He is first seeking guidance from the ECJ on the interpretation of the Software Directive. The key issues are whether programming languages, interfaces and functions are protectable by copyright. All the questions revolve around the fundamental copyright principle that ideas are not protected, only the expression of ideas. Here’s a rough expression of the ideas underlying the judge’s questions:
This is not the end of the story, however. The judge’s views are conditional. He is first seeking guidance from the ECJ on the interpretation of the Software Directive. The key issues are whether programming languages, interfaces and functions are protectable by copyright. All the questions revolve around the fundamental copyright principle that ideas are not protected, only the expression of ideas. Here’s a rough expression of the ideas underlying the judge’s questions:Programming languages: are they idea or expression?
Interfaces: the Software Directive makes some concessions for the fact that computer programs need to interface with each other. But are interfaces completely unprotected by copyright?
Functions: copyright may protect not just the software’s source code but also its design. To what extent can software be eligible for the type of copyright protection that is extended to the plot of a novel? How far can functionality be equated with design/organization?
Smoking pipes and other copyright tales

To the USA first, where the Recording Industry Association of America (RIAA) have announced that they will appeal a federal judge's reduction of a file-sharing copyright damages award from $675,000 to $67,500 in the Joel Tenenbaum case. The original award ordered the Boston University student to pay $675,000 in copyright infringement damages for sharing 30 songs online. Earlier this month, U.S. District Judge Nancy Gertner ruled that amount unconstitutionally excessive, and reduced it by 90%. Similarly the copyright infringement damages award of $1.92 million that a jury ordered defendant Jammie Thomas-Rassett to pay has been reduced $54,000, although that case appears headed for a new trial on the issue of damages.
An to Germany for another turnaround: In Dusseldorf the appellate court has overturned a lower court's order that free file-hosting service Rapidshare must install a keyword filter to block the sharing of copyrighted media. The lower court issued a preliminary injunction against Rapidshare last year, after film distributor Capelight Pictures sued the site when copies of its "Insomnia" and "Inside a Skinhead" movies were made available for download from the service. The lower court ordered Rapidshare to filter words such as "insomnia" and "skinhead". The Higher Regional Court of Dusseldorf has now ruled that more advanced filter that used full film titles cannot be used - noting that the words could wrongfully remove users' private copies of the films, which are permitted under German law. The court also said Rapidshare is not obligated to pursue those who distribute links to unauthorized files hosted on it service.
Finally to Eire where Irish ISP UPC has said that it will continue to “vigorously” defend itself against liability proceedings taken against it in the Eire's courts by content owners. The company is the latest in a series of ISPs to take issue with copyright holders' insistence that they police customers' Internet traffic. Ireland's biggest ISP, Eircom, was successfully taken to court by the IRMA (Irish Recorded Music Association) and is currently sending warning letters to customers who have allegedly infringed copyright through illegal downloading using the IP addresses of alleged infringing customers which are supplied by IRMA. UPC said that it does not condone piracy, but considers that "there is no basis under Irish or European law requiring an ISP to monitor or block subscriber traffic on its network" – although in France and the United Kingdom there are the new, and much criticised, "three strikes" laws – the French HADOPI law and the Digital Economy Act in the UK – the French law has already faced legal challenge and as previouslt reported, the UK law is about to face a judicial review.
http://www.zeropaid.com/news/90025/riaa-appeals-reduction-of-tenenbaum-p2p-judgment/
http://arstechnica.com/tech-policy/news/2010/07/german-court-overturns-injunction-against-rapidshare.ars
http://www.pcworld.com/businesscenter/article/201767/isps_battle_against_threestrikes_rule_throughout_eu.html
Friday, July 23, 2010
Copyright: a help or hindrance?
 "Driving UK Research – Is copyright a help or a hindrance?" is the title of a new report from what is termed "the research community", compiled by the British Library. It examines the UK’s existing intellectual property framework, "reflecting the challenges researchers face on a daily basis and highlighting a consensus across all sectors on the need for reform to meet the demands of a modernising world". According to the media release yesterday,
"Driving UK Research – Is copyright a help or a hindrance?" is the title of a new report from what is termed "the research community", compiled by the British Library. It examines the UK’s existing intellectual property framework, "reflecting the challenges researchers face on a daily basis and highlighting a consensus across all sectors on the need for reform to meet the demands of a modernising world". According to the media release yesterday, "Sourced directly from researchers this report presents a ‘grassroots view’ of the current copyright framework in the UK. Looking at the barriers they encounter on a daily basis, the contributors’ feedback not only highlights the obstructions to creativity but also puts forward proposals for reforming UK intellectual property legislation to reflect the needs of today’s researcher.You can read it here. It's 19 pages long and, despite its brevity, covers quite a broad range of issues. My impression is that this set of mini-essays represents the view of the high end of the research community, the respectable zone in which researchers are sufficiently attentive to the impact of copyright law to want (i) to avoid infringing it and (ii) to change it where possible to bring its provisions more closely into accord with modern research techniques and computer-driven facilities. The low end of the research community just gets its head down and carries on researching on the assumption that -- with the exception of gaining access to necessary sources and materials -- copyright is no problem because it can be safely ignored.
Dame Lynne Brindley, Chief Executive of the British Library, [says]:
“Underpinning research in the UK, the British Library presents this report on behalf of the research community, raising their thoughts and ideas on how to create a copyright system fit for the future. We hope it will provide a useful contribution to the debate.”
Thursday, July 22, 2010
HTC Aria Social Networking Smartphone
 It starts with a single block of jet black aluminum that forms the smooth and seamless case of the Aria. Small enough to fit in your shirt pocket. Powerful enough to use for both business and personal needs. Its large 3.2 inch touchscreen features pinch-to-zoom, which automatically reflows text for easy reading as you zoom in and out of websites.
It starts with a single block of jet black aluminum that forms the smooth and seamless case of the Aria. Small enough to fit in your shirt pocket. Powerful enough to use for both business and personal needs. Its large 3.2 inch touchscreen features pinch-to-zoom, which automatically reflows text for easy reading as you zoom in and out of websites.Yes, this is an Android smartphone. It runs Google’s Android 2.1 operating system and HTC Sense user interface. You can create and save multiple customized home screen layouts. You’ll be able to access thousands of apps and widgets on the Android Market. The Aria comes to you preloaded with Google Maps, Gmail, Google Talk, search and YouTube video access. Being on the AT&T 3G network, you’ll be able to surf and talk at the same time. That’s not true on all cellular networks.
The HTC Aria is set-up for messaging. The Email client accesses and syncs your corporate Email, Push Gmail and POP/IMAP regular email accounts. Or use your Web-based email account. There’s an HTML Web browser that gives you PC-like viewing and navigating of the Web with pinch and zoom capability. Multimedia messaging lets you send and receive picture and video messages. You’ll take some nice ones with the built-in 5 Megapixel autofocus digital camera that doubles as a camcorder.
The Aria is loaded with connectivity. It works on the worldwide GSM standard networks at 850, 900, 1800 and 1900 MHz. It also supports UMTS on 850 and 1900 MHz. You’ll be downloading at 3G speed over the AT&T HSDPA network. Want even more speed or to save your data plan? Use the WiFI capability with AT&T HotSpot support.
Mind you, this is a small phone that weighs-in at just 3.9 ounces. Dimensions are 4.1 x 2.3 x 0.5 inches. Yet it sports 384 MB of RAM and expandable to 32 GB using plug-in microSD memory cards.
Like Music? you can stream stereo music to and from A2DP compatible Bluetooth devices. The MP3 player supports AAC, MP3 and WAV formats. It’s also a high performance streaming multimedia phone. Watch full length TV shows with AT&T Mobile TV and stream music and videos.
Does this sound like the kind of high performance phone you’ve been looking for but not sure you can afford? Relax. You can get the HTC Aria for AT&T for FREE when you order it with new cellular service online.
Of course, there are many more free and low cost cell phones available to you right now. Check out the current specials and see what meets your needs. You’ll probably have a hard time picking just one.

Rightslink gets an upgrade
 It really is a busy time of year for online rights and licensing enthusiasts. Only yesterday we tasted the pineapple with Eric E. Johnson's konomark -- which got a bit of a thumbs-down from our readers -- and Creative Commons issues are never far from the surface of our consciousness, particularly now that we have the uncommonly creative Aurelia in our blogging team. Now it's the turn of the Copyright Clearance Center, which has announced the upgrade of its online licensing tool Rightslink: this lets content users obtain instant gratification in their quest for reprint and permission services by going directly to publishers’ websites. According to CCC,
It really is a busy time of year for online rights and licensing enthusiasts. Only yesterday we tasted the pineapple with Eric E. Johnson's konomark -- which got a bit of a thumbs-down from our readers -- and Creative Commons issues are never far from the surface of our consciousness, particularly now that we have the uncommonly creative Aurelia in our blogging team. Now it's the turn of the Copyright Clearance Center, which has announced the upgrade of its online licensing tool Rightslink: this lets content users obtain instant gratification in their quest for reprint and permission services by going directly to publishers’ websites. According to CCC, "The new version of Rightslink includes new features that make it easier for publishers to provide their users with the ability to obtain reprints through their respective sites. Rightslink customer emails have also been upgraded to a new look and optimized functionality. In addition, Rightslink also allows users to obtain reprint permissions “on the go” via the iPad, Nook and other mobile devices that support JavaScript. With knowledge professionals consuming content on evolving digital formats and publications creatively exploring new business models that include the iPad and other mobile devices, Rightslink makes it possible for publishers to monetize content wherever it is displayed".So now you know. If readers have any pensées on the issues arising, or on Rightslink itself, I hope they will share them with us.
Reclaiming the Rights that are Left - Corrected
Note on Corrections: Yesterday, I posted about jazz musician Frank Foster’s reclaiming of his copyright in the song “Shiny Stockings”. But, I cited and applied the wrong law, Section 203 of the US Copyright Act instead of Section 304. Section 203 applies to rights transferred after 1977, not before 1978 as I had stated. A very nice gentleman at the US Copyright Office was kind enough to bring this to my attention. The corrected post is below.
-----------------------------
There’s a great story over at Jazz Corner about an artist protecting his rights under the US Copyright Act. Often, criticisms of serving big companies and leaving the artists out in the cold are leveled at the Copyright Act, so it’s nice to see an occasion where the Act is working positively for the artist.
The Artist
Jazz Corner’s report does a nice job of covering the humanitarian side of the story. I’ll offer a short summary here, but suggest you read the piece there for more information. Saxophonist Frank Foster wrote a very popular jazz tune called “Shiny Stockings.” And like many other musicians, he signed away the rights to the song without really knowing what he was giving up. (NPR story on that issue here.) But now, he is going to get his royalties with the help of the Community Law Clinic at Rutgers Law School. [A demo of the film documenting Foster’s story can be found here.]
The Work
When “Shiny Stockings” was penned in the mid-1950s, it was covered under the 1909 US Copyright Act. This Act provided copyright protection for a term of 28 years, with an option to renew for another 28 years. Before the first term could expire on “Shiny Stockings”, a new copyright act came into effect. The US Copyright Act of 1976.
The Law
The 1976 US Copyright Act made a number of substantial changes to the US copyright law. As such, the new act needed to provide for a variety of different situations, including protection of existing non-published works, works that had already been renewed once and works that were in their first copyright period under the 1909 Act. Section 304(c) provides a special protection for artists whose works fall under the second two categories.
Since the 1909 Act provided for two 28 year terms (with renewal), authors could transfer or license their rights for up to 56 years, the entire possible term of the copyright. The 1976 Act added extra years to the copyright term, years the authors didn’t know they would have when they transferred away their rights. So, the 1976 Act provided a way for authors to reclaim the extra years.
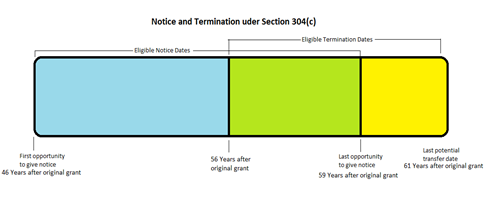
Under Section 304(c), authors who transferred their rights in a work prior to 1978 have an opportunity to take back their rights after the end of the term they thought they were giving away. The window for this opportunity opens at 56 years after the original copyright date and stays open for five years. Sort of. The author has five years within which to terminate the original grant, but the author has to give the grantee two-years written notice. (Notice must also be given to the Copyright Office before the termination occurs.) Then, of course there’s another catch that makes the math more complicated. The notice can be sent out as early as ten years before the termination date picked by the author. So what the author actually winds up with is something like this: (click to view full scale)
“Shiny Shoes,” which was first copyrighted in 1956, so Foster could have requested transfer anywhere from 2012 to 2017. Once the transfer is effective, Foster will have all the rights which the original transfer had given away, until the end of the work’s copyright term. For “Shiny Shoes” that full term is 95 years, until 2051.* Foster and his heirs will get roughly forty years of copyright royalties that the otherwise wouldn’t have received. Not bad.
*The nice gentleman that send the correction also provided information that “Shiny Shoes” was renewed for its second copyright term in 1984, making it eligible for the 95 year full term under the Sony Bono Copyright Term Extension Act. See Section 304(b).
Again, my sincere thanks to the gentleman for his note, and my apologies to The 1709 Blog readers for the incorrect information in the previous post.
Wednesday, July 21, 2010
BPA / Bisphenol A
Food Safety Bill Saga Continues as Congress Bickers Over BPA Ban
Sen. Dianne Feinstein Trying to Add BPA Ban to Food Safety Legislation
Industry execs say there's no safe alternative to BPA, that's just not true. Eden Organic crafted BPA-free cans for its organic beans.
Feinstein's call for BPA ban bill riles lobbies
The Food and Drug Administration has not declared BPA a risk to public health at current levels. The agency said studies using standard toxicity tests "have thus far supported the safety of current low levels of human exposure to BPA." It said new tests using "novel approaches to test for subtle effects" raise "some concern" and called for more studies.
Feinstein's legislation would put pressure on the industry to find an alternative by granting companies a renewable one-year waiver while they try to find a substitute and requiring in the meantime that they label their products as containing the chemical.
Thirty major chemical and food manufacturing industry groups have banded together to defeat Feinstein's efforts.